Implement Azure Role Assignment by AAD Application with Powershell Script
Implement Azure Role Assignment by AAD Application with Powershell Script

The requirement come with ask "Having an application(first application) created in AAD and want to use first application to assign roles to a second application created in AAD"
To achieve that goal, Azure active directory admin needs to grant below permission for first application's service principal.
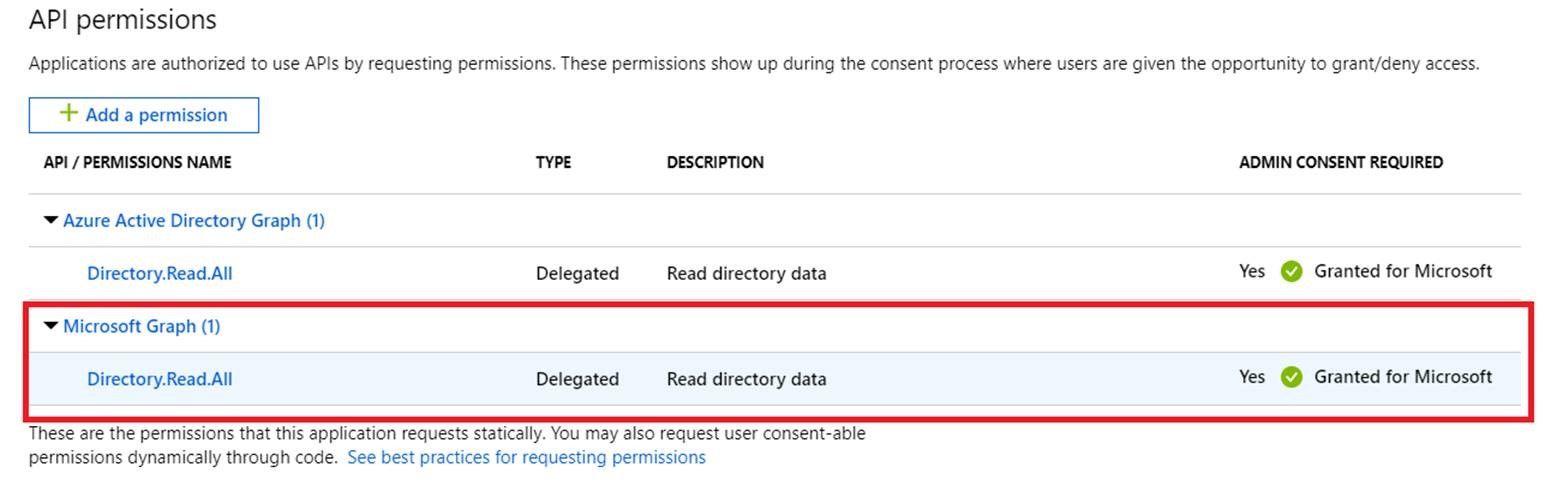
Then below script can be used to assign roles to second application for corresponding resource
# INPUT YOUR FIRST APPLICATION ID/SECRET
$creds = Get-Credential
$objId = <YOUR_SECOND_APPLICAITON_ID>
$tenantId = <YOUR_DIRECTORY_ID>
Connect-AzAccount -Credential $creds -ServicePrincipal -Tenant $tenantId
$spId = (Get-AzADApplication -ObjectId $ojbId | Get-AzADServicePrincipal).Id
New-AzRoleAssignment -ObjectId $spId -RoleDefinitionName Reader -Scope <YOUR_RESOURCE>
Some comments for above script:
- New-AzRoleAssignment requires
ObjectIdas a parameter, however, in AAD, Application Id is not an object id, to get object id, need to run$spId = (Get-AzADApplication -ObjectId $ojbId | Get-AzADServicePrincipal).Idto convert application id to service principal's object id. $spId = (Get-AzADApplication -ObjectId $ojbId | Get-AzADServicePrincipal).Idwill query AAD to map application id to object id, it requires AAD "Read Directory Data" permission, so need AAD admin to give permission to first application.

